Conscious decision to invest in Information Security
Information cyber is on the rise, and it is affecting the operation of the company and the decision which the top management is going to make. We will explore the Conscious decision to invest in Information Security.
There is a high awareness of the significance of having appropriate information security. Nonetheless, organizations tendto set this least important, placing their focus on their primary business operations till they experience some security occurrence. Besides, some of the measures put in place by these organizations are usually insufficient in dealing with the broad range of security risks.
The importance of assuring the security of information assets is becoming more critical every year. However, the critical areas of information security risk management and risk metrics still do not receive enough attention. Having some false senses of the security within an organization’s information consequently impacts on their information security; hence, their investment decisions. Since information security has not tobe placed as a toppriority within these firms, the firms tend to have restricted budgets, one of the most limited setsof the information security techniques and are more probable to place more focus on the fundamental operations. Once initial securities are in place, the firms are more unlikely to revisit the security concerns within the information unless there are some main security issues.With ISO standards as guidance, the practical aspects and sufficiency in evaluating the security mechanisms are classified in more detailed.
The notion that some of the information security program execution would have a significant effect on the efficiencyof an organization operations as well as the notion that information security is significant, organizations should tend to accomplish some balance in between upholding the security rules and not instigating any form of inconvenience within our workplace.
Positive impact:
The sound investment is always rejected because it can carries deterrent in case it fails to integrate appropriately intoour workflow as well as procedures. If time is taken into consideration of the processes and information security strategy is integrated within an organization procedureas well as operations with variousmindsets of personnel across all departments, it will develop a sound investment choice. Having established a baseline like diagnostic approach can help to make sound investment and save cost.
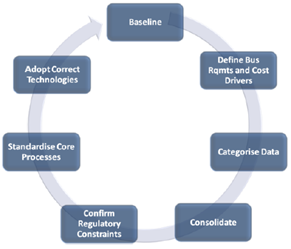
Extracted from: HOW DOES INFORMATION SECURITY IMPACT YOU? (trustedimpact.com)
The policy provides the rules that govern how systems should be configured and how employees of an organization should act in normal circumstances and react during unusual circumstances. As such, policy performs two primary functions:
- The policy defines the expected state of security within an organization.
- The policy puts everyone on the same page so what is expected is understood.
Policies and procedures establish guidelines forbehavior and business processes in accordance with an organization's strategic objectives. It can further be strengthened through stringent regulations, well-documented procedures, proper guidelines, and proven standards.
Human Resource Security, Personnel can also be regarded as business assets. People with their knowledge and skills are valuable assets, and measures are necessary to protect this value.
The organization must have rigorous procedures when personnel leave and enter employment, or when they change jobs within the organization. It is important to change or remove access rights when deem fit, and to collect equipment and passes that are expired - thus making access rights control a regular process in the information security. Three distinct phases in the evaluation:
Prior to Employment – organization can employ strict physical screening with a NDA in place in the interview process.
During Employment – awareness can be enforced through induction programs. Other means include flyers, booklets, messages on computer screens, mouse pads, newsletters, videos and posters. With information security courses targeted at certain groups, new social engineering tactics to gain confidential information via formal (company events) or informal (social drinking sessions) events in the corporate environment can be addressed and stopped.
Termination and Change of Employment – this is addressed via the employment contract where confidentiality of information maintains for 1 or 2 years after termination and rights to information are revoked immediately along with the return of all company assets.
Negative impact:
Companies are mainly reluctant in taking any form of risk while developing integrated information security systems that seemed uncommon or unpopular to them and in places where it is not executed in line with industry requirements. Such is viewed as poor execution of the information security program and might hinder the business operations.
Besides, companies have some false sense of securityprograms in their presenting security practices. Additionally, organizations were fully aware of some significance of safeguarding their systems and information through high-level standards as well as backup measures like installation of the virus-scanner. In fact, no single recognized event or occurrence has been in existence in the last three years that offered the companies a falsesense of securityto their information.
Compliance
Two areas of consideration: one involves compliance with the myriad laws, regulations or even contractual requirements which are part of the fabric of every institution; the other is compliance with information security policies, standards and processes.
Some common compliance measures include:
Observance of statutory regulations;
Intellectual property rights (IPR);
Protection of Personally Identifiable Information (PII);
Protecting data and the confidentiality of personal data;
Protection of data records;
Compliance with security policies and standards (eg. ISO, NIST, ANSI);
Conclusion
There are many more factors (e.g.Asset Management; Information Security Incident Management; Information System Acquisition, Development, andMaintenance; Communications and Operations Management ) for consideration in implementing a thoroughlyconcise and practical information security standards. What is important is that the procedures, policy, compliances, etc. are outlined and documented along with the ISO standards so that risks associated with implementing information security can be minimized – thus paving the way for a system that can be improved contextually.
Author: Tan Kian Hua, student LIGS University
Bibliography
Ashenden D. Information security management: a human challenge? Elsevier Information Security Technical Report 13; 2008
Australasian Conference on Information Systems (pp. 74‐84), Melbourne, Australia: Monash University. 2009.
Bandyopadhyay, K; Mykytyn, P; Mykytyn, K (1999) "A framework for integrated risk management in information technology,"
Briney, A., & Prince, F. (2002). Does Size Matter.
Cavusoglu, H., B. Mishra, and S. Raghunathan (2004): “The effect of internet security breach announcements on market value: Capital market reactions for breached firms and internet security developers,”
Dimopoulos, V., Furnell, S., Barlow, I. and Lines, B. (2004), “Factors affecting the adoption of IT risk analysis” June 2004.
Gehringer EF. Choosing passwords: security and human factors. In: ISTAS’02 international symposium on technology and society; 2002.
Gerber, M. and von Solms, R (2005). "Management of risk in the information age."
ITGovernance Institute. Information security governance: guidance for information security managers. ITGI Publishing; 2008.
International Organization for Standardization. ISO/IEC 27001: 2005. ISO; 2005.
Johnston, A.C. & Warkentin, M., 2010. Fear Appeals and Information Security Behaviors: An Empirical Study.
Lacey D. Managing the human factor in information security: how to win over staff and influence business managers. John Wiley & Sons,Inc.; 2009.
Nguyen, N. & Leblanc, G. (2001), “Corporate image and corporate reputation in customers’ retention decisions in services”.
NIST. (2009). "Recommended Security Controls for Federal Information Systems and Organizations."
Mitnick KD, Simon WL. The artof deception. John Wiley & Sons, Inc.; 2003.
Sasse MA, Brostoff S, Weirich D. Transforming the ‘weakest link’ a human/computer interaction approach to properand adequatesecurity. July 2001.
Scholtz T, Byrnes FC, Heiser J. Best practices and common problems for information security programs. Gartner; 2006.
Shedden, P., Ruighaver, A.B., Ahmad, A., (2006) Risk Management Standards ‐ The Perception of Ease of Use.
Shedden, P, Scheepers, R., Smith, M., Ahmad, A. (2009) Towards a Knowledge Perspective in Information Security Risk Assessments – an Illustrative Case Study, Proceedings of the 20th
Siponen, M. & Vance, A.O., 2010. Neutralization: New Insights into the Problem of Employee Systems Security Policy Violations.
Tipton HF, Krause M. Information security management handbook. Auerbach Publications; 2007.
Williams P. In a ‘trusting’ environment, everyone is responsible for information security.; 2008.
Wood CC. Information security policies made easy.; 2002.